Securing cloud computing environment in 2024: Techniques, tips, and best practices
Cloud computing is a scalable and cost-effective way to host your data and applications, which is why 75% of businesses plan to migrate to the cloud by 2026.
However, while a cloud environment has multiple benefits, it poses certain security risks. The 2023 Cloud Security Report by ISC2 found that 95% of businesses are concerned about cloud security, making it a top concern for enterprises.
If you use a cloud-based infrastructure or are planning to migrate to the cloud, it’s essential to understand its security risks and how to mitigate them. In this guide, you’ll learn what to look for in cloud security and its best practices.
Let’s dive in:
Cloud security 101
Cloud security encompasses the tools, protocols, and technologies used to secure a cloud computing environment. These security measures protect a company’s cloud-hosted data and applications from malicious actors, unauthorized access, and data loss.
Unlike a traditional enterprise network where physical servers are located on the company premises, cloud computing servers are located in remote data centers. Depending on your chosen cloud service provider (CSP) and the service you opt for, your business might have limited access to these servers, so ensuring server security might be challenging.
In a traditional enterprise network, users access the data and applications through the enterprise’s network. In a cloud environment, users may utilize public networks, and it might lead to cloud security vulnerabilities.
Most cloud environments use a multi-tenant architecture, where different businesses run their applications on the same server. Because multiple users share server resources, your business may become vulnerable to security threats, data breaches, and performance issues.
To fully understand how to mitigate these risks, let’s dive into how cloud security works.
How does cloud security work?
A cloud environment is a complex system with multiple layers, such as the infrastructure, platform, and application layers. An effective cloud security strategy incorporates tools and techniques to prevent data breaches and malicious attacks at each layer.
Let’s explore these cloud computing layers and the main security measures to implement.
1. Infrastructure layer
The infrastructure layer comprises the physical servers hosting the cloud environment and the network devices interconnecting these hosts.
The cloud security measures to implement at the infrastructure layer include:
- Restricting physical access to the servers.
- Ensuring correct configuration of physical servers and network devices.
- Updating server operating systems and software.
2. Platform layer
The platform layer runs on top of the infrastructure layer and provides an environment for application development, deployment, and testing. The operating system and application framework are two main parts of the platform layer.
Securing your cloud computing environment at the platform layer involves:
- Creating user groups and roles to prevent unauthorized access.
- Implementing authentication mechanisms like multi-factor authentication (MFA).
- Monitoring user activities to detect threats and unauthorized access.
3. Application layer
The application layer encompasses a set of applications that access and modify user data to perform specific functions.
The following practices prevent data leaks and unauthorized application changes at the application layer:
- Data encryption.
- Controlling user privileges.
- Securing application programming interfaces (APIs).
The shared responsibility model for cloud security
Depending on the cloud service and the hosting model, the CSP and the customer share the security responsibilities as follows:
- Infrastructure-as-a-Service (IaaS): The CSP secures server hardware and maintains the servers by configuring and patching them. The client is responsible for securing their operating systems, data, and applications.
- Platform-as-a-Service (PaaS): In the PaaS model, the CSP offers the operating system and application framework as a service. The CSP secures the physical hardware, the application framework, and the operating system while the client secures their applications.
- Software-as-a-Service (SaaS): The CSP provides ready-to-use applications hosted on the cloud. It secures the server hardware, operating system, and applications while the client ensures secure user access to these applications.
Why is cloud security important?
A secure cloud computing architecture ensures regulatory compliance, strengthens your brand’s reputation, ensures continuity, and protects business-critical data. Let’s consider these benefits in detail.
Regulatory compliance
Governments across the globe are imposing strict laws to ensure data privacy. In 2023, eight U.S. states passed robust consumer privacy regulations.
This is in addition to long-standing state-specific regulations, like:
- California Consumer Privacy Act.
- Colorado Privacy Act.
- Virginia Consumer Data Protection Act.
If you’re running a global business, you must also adhere to region-specific regulations like the General Data Protection Regulation (GDPR).
An effective cloud security strategy lets you stay compliant with these regulations and avoid fines and legal suits. These regulations prompt businesses to develop guidelines and policies that will create a secure cloud environment in the long run.
Business continuity
Cloud security protects sensitive information and files from data leaks and malicious attacks (e.g., malware and phishing), ensuring your business can always access its data.
By implementing strict data protection measures, your business can maintain its operations without being significantly impacted by security breaches, power outages, natural disasters, and other disruptions.
Customer trust
A business that operates in an unsecured cloud environment is prone to data leaks. Cybercriminals can use leaked customer data (e.g., personal, financial, or health information) to commit identity theft or fraud. This can lead to reputational damage and loss of customer trust.
By contrast, a secure cloud computing environment enhances brand reputation, making it easier for customers to trust your business with sensitive information.
Data security
Businesses often store sensitive data like project roadmaps, designs, and research documents in the cloud infrastructure. If there’s a cybersecurity breach, an intruder might gain access to this data and delete it or hold it for a ransom.
Cloud security policies can help you identify and mitigate risks. This protects your intellectual property from unauthorized access, giving you a competitive advantage.
What are the security risks of cloud computing?
- Wider attack surface.
- Lack of cloud visibility and control.
- Complex configuration.
- Multitenancy.
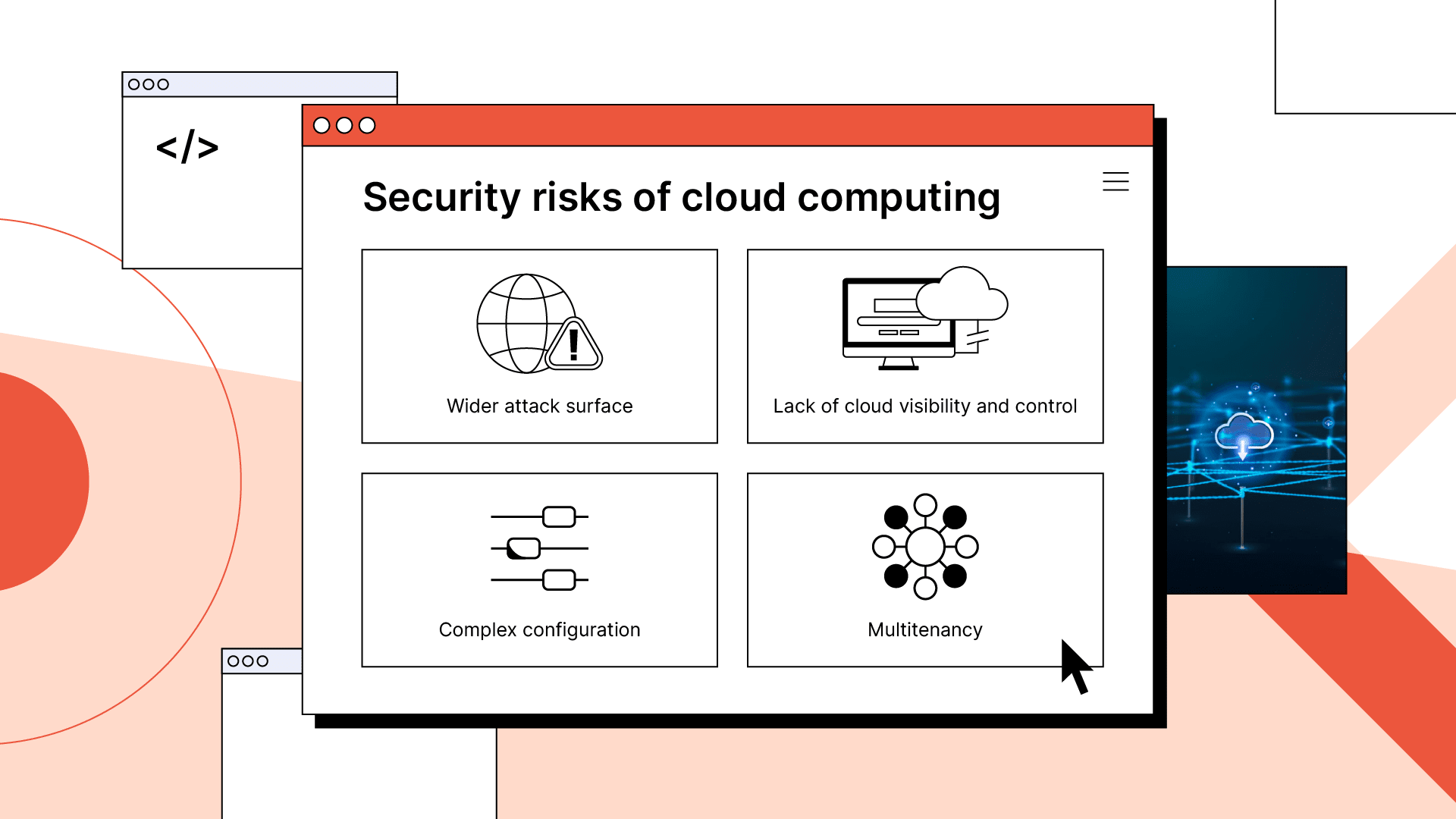
While cloud computing offers scalability and flexibility, its distributed model and virtual servers pose some security challenges.
Wider attack surface
An attack surface includes all the network endpoints vulnerable to an attack. Businesses with an on-premise infrastructure have tighter control over their physical servers and enterprise networks. This narrows the attack surface.
In a cloud environment, virtual servers are added and deleted dynamically. There is a chance of server misconfiguration, making these servers susceptible to attacks and thus widening the attack surface.
When businesses use a cloud service provider, they have limited visibility over who is accessing the cloud environment and from where. Users might utilize unsecured networks and devices, heightening the chances of an attack.
Lack of cloud visibility and control
The cloud is a complex environment where multiple users log in from different locations. If your business uses a SaaS or PaaS cloud service model, it might not get complete information on who is logging in to the cloud environment.
Further, in PaaS and SaaS models, a cloud service provider handles a significant part of cloud security, so your business might not know about potential cyberattacks, nor can it detect or prevent them.
Complex configuration
A cloud environment might contain hundreds or even thousands of virtual machines. Each machine should have the correct security configurations (e.g., passwords, user groups, roles, and access controls) to protect sensitive information.
In a 2023 cloud security report, Cybersecurity Insider identified the lack of experienced staff as the top cloud security barrier for companies. To prevent misconfigurations, you can either invest in employee training or hire external experts with specialized cloud security experience.
Multitenancy
In a public cloud environment, a business shares a physical server with several other users.
This could lead to security issues like:
- A co-tenant initiating an attack.
- An attack aimed at a co-tenant affecting the other tenants.
- A co-tenant’s security breach making the cloud environment vulnerable to attacks.
Even though CSPs provide isolation, there is a security risk associated with multi-tenant environments. A private cloud is a great option to avoid the vulnerabilities of multitenancy — you get exclusive access to your cloud environment.
While there are some risks associated with cloud computing, choosing the right solution can help you maintain a solid cloud security posture.
What to look for in cloud security
- Identity and access management (IAM).
- Threat monitoring and prevention.
- Advanced data protection.
- Security information and event management.
- Data loss prevention.
- Disaster recovery solution.
Securing the cloud computing environment is a top priority for enterprises. Here are the critical elements of cloud security you should look for.
Identity and access management (IAM)
A cloud environment will have users logging in from around the globe using unsecured devices and public networks. Hence, attackers can pretend to be legitimate users.
This makes identity and access management a crucial part of cloud security. IAM has multiple access control techniques to ensure only legitimate users can log in to a cloud network.
These include:
- Role-based permissions and user privileges.
- Multi-factor authentication and the enforcement of strong passwords.
- Dynamic updation of user access privileges with business changes.
- Continuous monitoring of login activity and reporting of suspicious activities.
Threat monitoring and prevention
Advanced technologies like intrusion detection systems (IDS) and intrusion prevention systems (IPS) can detect potential threats and take countermeasures.
The IDS will monitor your cloud environment and flag any activity that matches a cyberattack signature. This includes abnormal changes in access privileges and the general slowing down of the network.
The IDS can detect various cloud security breaches like:
- Distributed denial of service (DDoS).
- Man-in-the-middle (MITM) attacks.
- Zero-day attacks.
- Malware attacks.
- Insider threats.
The IPS complements the IDS by playing a more proactive role. It prevents attacks by dropping malicious packets and blocking suspicious users, in addition to other techniques.
Advanced data protection
Data protection is an essential feature to look for in cloud security. It protects data from unauthorized access, data breaches, and data loss.
Encryption is the primary technique used to protect data in a cloud environment. It involves coding the data into an unreadable format, which can only be deciphered with a secret key.
There are two types of data to consider in a cloud setup, and each requires a different encryption method:
- Data at rest: Use an encrypted hard disk to store data. The cloud security solution will encrypt the data while writing into the disk.
- Data in transit: Use SSL/TLS technologies to encrypt data while it travels from the server to the client or vice versa.
You may also use public key infrastructure (PKI) to issue digital certificates. The digital certificate helps applications ensure the legitimacy of incoming data. You may assign digital certificates to a user, device, or application.
Security information and event management (SIEM)
The SIEM system collects log data from the entire cloud environment and collates it in a centralized platform. You can use this data to automate security monitoring and threat detection in the cloud environment.
SIEM uses artificial intelligence and machine learning to analyze your log data and detect suspicious activities.
Data loss prevention (DLP)
Losing business-critical data may result in financial setbacks, regulatory fines, legal suits, and damaged customer relationships. According to IBM, data loss cost companies $4.45 million in 2023.
Using predefined data types or templates, DLP classifies customer data like credit card or social security numbers, helping organizations comply with data protection regulations. It also uses techniques like de-identification, tokenization, and masking to reduce cloud security risks.
Disaster recovery solutions
A disaster recovery system backs up critical data so a business can restore the data lost during a natural or man-made disaster.
A disaster recovery system has three elements:
- A preventive element continuously monitors the cloud environment, looking for configuration errors or compliance violations.
- A detective element identifies data loss in real time and automates recovery.
- A corrective element plans for potential disasters and routinely backs up critical data and apps.
Cloud security best practices
To secure cloud computing environments, businesses and CSPs must follow cloud security best practices, use the right tools, and adopt the right technologies. Let’s explore these best practices.
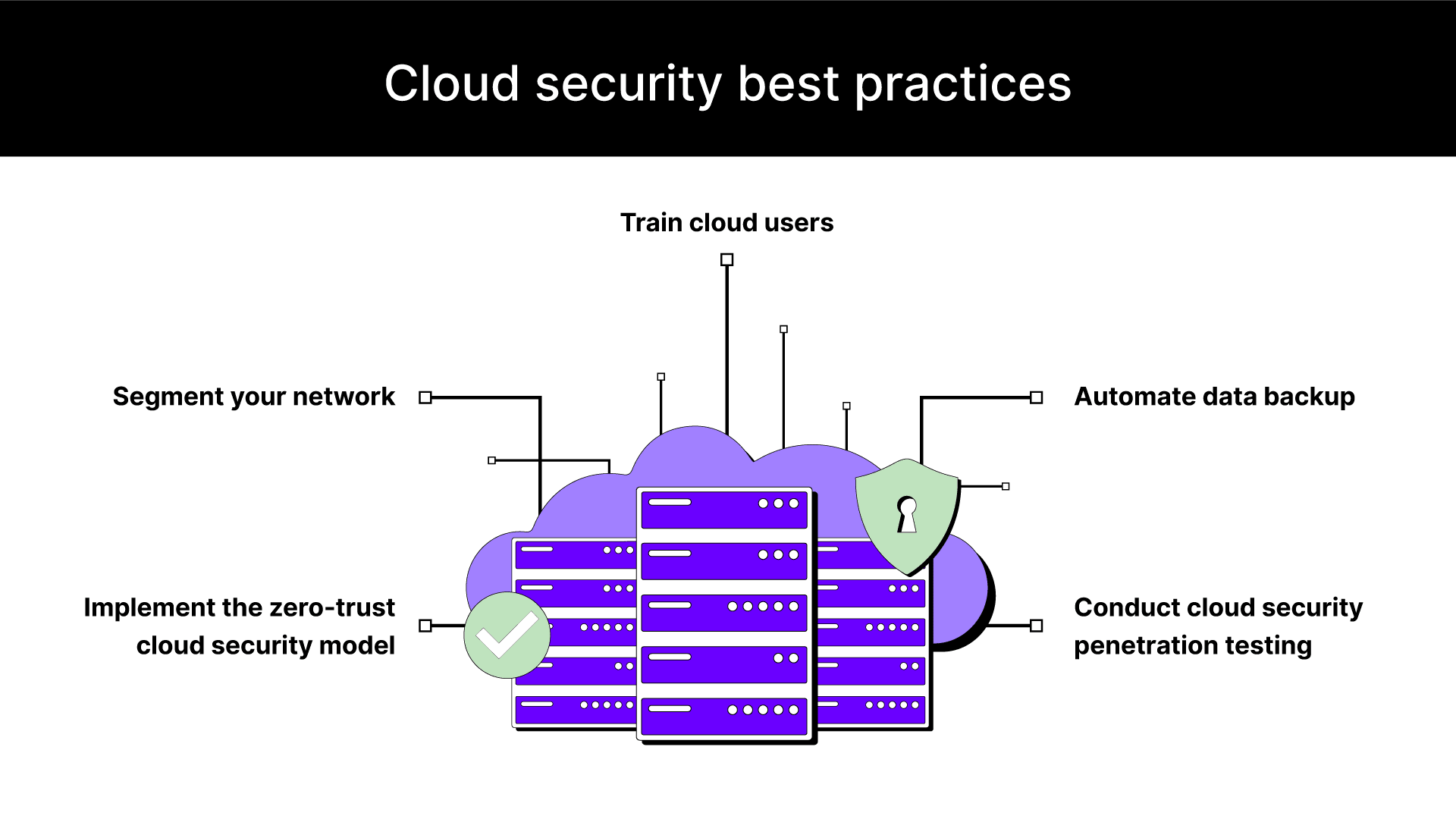
Implement the zero-trust cloud security model
The zero-trust protocol gives users just enough access privileges to get their jobs done. Users who have more privileges than they need might not be aware of data protection strategies and might unintentionally leak critical information. Attackers might also target such user accounts to gain access to your cloud environment.
Along with minimum necessary privilege, the zero-trust protocol mandates the authentication of every user, no matter where they access the network from. It authenticates users based on several parameters, such as their credentials, location, and device health.
Segment your network
Segmentation is the process of dividing your cloud network into subnetworks based on the information it contains and the workloads it runs. You can create cloud network segments for each department or at a workload level. Firewalls between segments will prevent malicious data packets from transmitting from one segment to the other.
Network segmentation is a good practice to prevent an attacker from destroying your entire cloud environment. To access your data, the attacker needs to breach segment by segment, which is difficult and time-consuming. Whenever there’s a data breach, you could isolate that segment, preventing the attack from progressing.
Conduct cloud security penetration testing
Penetration testing is an ethical hacking method used to evaluate the strength of your cloud security. In penetration testing, a tester (or a hacker) studies your cloud network and identifies weak points to exploit.
Here’s how it works:
- The tester identifies potential security vulnerabilities in a cloud environment.
- They exploit these vulnerabilities to launch an attack.
- The tester observes how the cloud network responds to the threat.
- The tester submits a report to the organization’s cybersecurity team.
Regular penetration testing will help you assess your cloud security posture and prepare for real-life attacks.
Automate data backup
Creating regular data backups is an effective way to secure a cloud computing environment. Many cloud service providers include data backup in their services. But in cases where it’s not included, it’s crucial to create your own backup routine.
Data backup ensures business continuity even during a malware or ransomware attack. Automating backups will eliminate the need for your IT team to be involved in day-to-day backups, saving you time and resources.
Train cloud users
A cloud environment has various users, including employees, contractors, and business partners. A user’s lack of cloud security awareness might lead to vulnerabilities, so 74% of businesses are concerned about data loss due to untrained users.
Here’s how to train cloud users:
- Enable multi-factor authentication wherever possible.
- Encourage the use of strong passwords and frequent password changes.
- Enforce the use of network and application firewalls.
- Train them to detect and report phishing attempts.
Training users to adhere to cloud security best practices reduces the risk of human errors and ensures compliance with relevant regulations.
Final thoughts: What to look for in cloud security
Cloud-based infrastructure is a highly flexible solution that can help you scale your business with ease. But it is also vulnerable to security threats like malware, ransomware attacks, and data leaks. Hence, cloud security should be a top priority for businesses that rely on cloud computing.
While your CSP handles some cloud security responsibilities, you can ensure maximum security by implementing the zero-trust policy, automating data backups, conducting penetration testing, and training your users.
However, securing your cloud computing environment starts with choosing the right service provider. If you’re looking for a cloud service provider that guarantees scalability, maximum security, and high performance, check out Liquid Web Cloud Studio today.
Related Resources

Luke Cavanagh
Product Operations Manager at Liquid Web. Devoted husband and Tween wrangler. Synthwave enthusiast. Jerry Goldsmith fan. Doctor Who fan and related gubbins.
Keep up to date with the latest Hosting news.



